Table of Contents
- Why Web3 Identity Matters
- Core Identity Fundamentals
- Security And Privacy Foundations
- Standards And Protocols
- Platform And Vendor Survey
- Real-World Use Cases
- Developer Implementation Guide
- Governance Recovery And Control
- Future Trends And Outlook
- Common Questions Answered
- Next Steps For Adoption
Why Web3 Identity Matters
Target Audience And Scope
As the internet architecture rapidly evolves, web3 digital identity management is fundamentally transforming how people, businesses, and entire industries think about online trust and presence. This guide is tailored for developers, product and technology leaders, marketers, entrepreneurs, and privacy-focused users who are eager to exert more control over their digital lives. You will learn how decentralized identifiers (DIDs), verifiable credentials (VCs), and self-sovereign identity principles—with human-friendly web3 domains—provide the backbone for user-controlled, censorship-resistant identity.
Importantly, this shift directly affects use cases like secure client onboarding, *regulatory compliance*, and innovative approaches to authenticating users, partners, and devices. That means developers building for web3 affiliate marketing platforms gain new tools for consent, transparency, and attribution. Product teams can foster more seamless, portable user journeys, and privacy advocates will discover tangible frameworks to advance digital autonomy. Throughout, we’ll reference W3C, Ethereum, and industry standards, plus major open-source and commercial ecosystems.
Key Concepts At A Glance
- Decentralized Identifiers (DIDs): Blockchain-anchored, user-generated digital identifiers that can be created and managed without centralized authorities (W3C DID Core).
- Verifiable Credentials (VCs): Digitally signed claims about people, organizations, or assets that can be selectively disclosed and cryptographically verified (Dock Web3 Identity).
- Self-Sovereign Identity (SSI): An identity model where users, not platforms, maintain ultimate control over their data, consents, and relationships.
- Web3 Domains: Human-readable blockchain domain names (like
.ethor hashtag domains) used as identity anchors, login handles, wallet addresses, and brand assets (NFT Domains Explained and Web3 Domain Services). - Zero-Knowledge Proofs (ZKPs): Cryptographic protocols that allow you to prove facts about yourself (e.g., age, credentials) without sharing private details (Zero-Knowledge Proofs Feature).
Technical Foundations: Blockchain ensures data immutability, distributed consensus, and cryptographic key management. Real-world applications include healthcare consent, financial onboarding, supply chain audits, and *loginless* commerce journeys. The tools and references cited will prepare you to pilot, build, or govern these new identity systems confidently.
Core Identity Fundamentals
Decentralized Identifiers Explained
Decentralized Identifiers (DIDs) are the keystone of web3 digital identity management. A DID is a globally unique identifier made and owned by users, without permission from any central gatekeeper. DIDs are accompanied by DID Documents, which detail cryptographic public keys, verification mechanisms, and service endpoints. DID Methods—like did:ethr for Ethereum, did:web for web-hosted DIDs, and did:key for key-derived identifiers—let you select a stack best suited to your project or community.
Resolvers are software engines that translate DIDs into their associated documents, enabling cross-platform interoperability and real-time updates. This flexibility is crucial for adapting identity to user needs, regulatory demands, or changing application environments.
Table: DID Standards Comparison
| Standard | Primary Use | Interoperability | Notes |
|---|---|---|---|
| DID Core (W3C) | Foundation spec for DIDs | High if method-compliant | Canonical reference for implementers |
| did:ethr | EVM-native, on-chain DIDs | Medium; EVM-specific tooling | Well-suited for Ethereum dApps |
| did:key | Key-derived, lightweight | High; no resolver required | Simple, not for large-scale use |
| did:web | DNS/HTTPS-based DIDs | Medium, uses existing web infrastructure | Good bridge for web-native services |
(Source: W3C DID Core, Ethereum Decentralized Identity, Endless Domains Ownership)
Verifiable Credentials And Claims
A *verifiable credential* (VC) is a signed digital statement about a subject—think “Alice graduated,” “Acme is certified,” or “Bob is over 21.” VCs are issued by trusted entities, held in secure user wallets, and presented to verifiers (apps, companies, governments) for review. Thanks to cryptography, the verifier can check the claim’s legitimacy without reaching out to the issuer or seeing unnecessary personal details. Selective disclosure and cryptographic proofs lie at the heart of this privacy-preserving approach (Dock Web3 Identity).
Self-Sovereign Identity Principles
Self-Sovereign Identity (SSI) is a user-centric paradigm: you alone create and manage your identifiers, credentials, and consent policies. Key SSI principles include portability (using identity across apps), interoperability, consent-driven data sharing, minimal disclosure, and *user agency*. Did you ever imagine controlling every login, credential, and profile update across the web, simply by managing your own private keys? With SSI, this vision comes closer to reality every day.
Web3 Domains As Identity
Web3 domains—like those offered by Web3 Domain Platform or NFT Domains Explained—transform abstract cryptographic identities into human-friendly, brandable handles. Mapping a wallet, DID, or VC to a domain lets people transact, communicate, or authenticate intuitively. Your domain becomes your single point of trust, supporting loginless authentication, decentralized payments, and seamless integration across apps.
From brand protection and anti-censorship to affiliate marketing, web3 domains let you manage not just *access* but your evolving digital identity and its value.
Centralized Vs Decentralized Models
Traditional models—OAuth, SAML, and enterprise identity providers—centralize trust, requiring you to rely on third parties to manage authentication. The web3 approach flips this: you become your own identity provider, mitigating lockout risks, censorship, and vendor dependency. Selective disclosure, claim provenance, and real-world credential mapping make this not only safer in many use cases, but often more efficient and portable as well (DevTo EveryCred Guide).
Security And Privacy Foundations
Identity in web3 is underpinned by cryptographic rigor and the unique properties of blockchain. Let’s explore how these technical layers guarantee privacy, immutability, and ownership.
Blockchain Anchoring Benefits
Anchoring proofs and metadata on blockchain provides tamper evidence and auditability—no single entity can rewrite or erase attestation histories. This is a game-changer for fraud prevention in supply chain, finance, and healthcare audits (IBM Verifiable Supply Chain), where verifiable claims streamline compliance and regulatory reporting.
Cryptography And Key Management
At the core are *public/private key* cryptosystems: you use private keys to sign credentials or transactions, while public keys enable others to verify those signatures. Advanced identity architectures use hardware wallets, key rotation, and multisig (multi-party signing) for extra resilience. Mismanaging keys is the biggest risk—yet, well-designed wallet flows and recovery solutions can empower users without excessive friction (Microsoft Decentralized Identity).
Effective key management in self-sovereign models transforms “identity as a service” into *identity as a right*—but requires both robust technical design and user-centered experience.
Zero-Knowledge Proofs In Identity
Zero-Knowledge Proofs Feature (ZKPs) enable credentials to be *proven*—e.g., showing someone is over 18—without revealing more than necessary. ZKP-backed credentials drive compliant KYC, age verification, and enterprise onboarding, all while shielding sensitive data.
Privacy Techniques Comparison
| Technique | What It Protects | Trade-Offs | Use Cases |
|---|---|---|---|
| On-Chain Hashing | Integrity & tamper-evidence | Immutable footprint, linkability risk | Audit logs, timestamping, credential anchors |
| Off-Chain Storage | Confidential personal/enterprise data | Needs trusted storage, data access | Medical records, supply chain manifests |
| Zero-Knowledge Proofs | Private attribute proofs | Higher compute, tooling complexity | Age/attribute gating, selective disclosure |
| Revocation Registries | Use of revoked credentials | Complexity, availability issues | Employment, certifications |
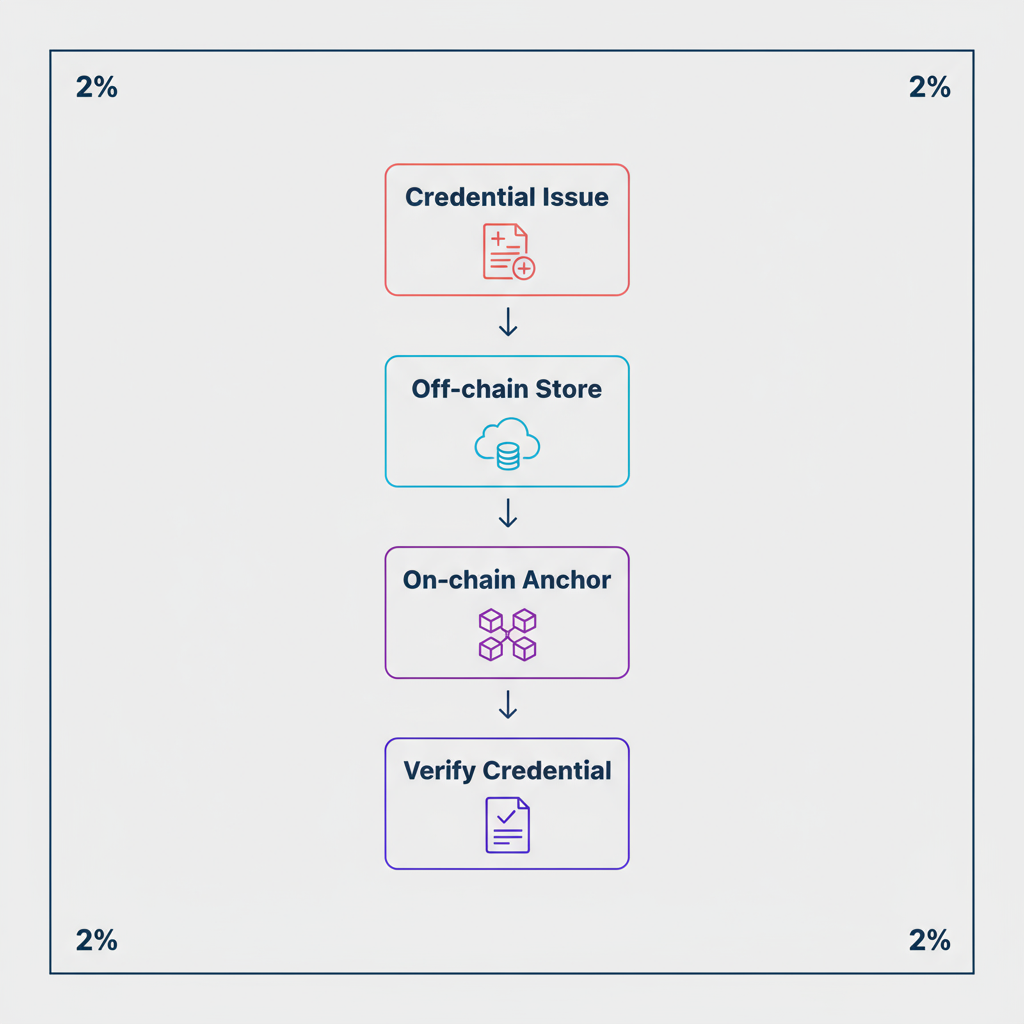
Threat Models And Mitigations
The distributed nature of web3 identity reduces single points of failure, but introduces new threats: replay attacks, key compromise, Sybil attacks, and access governance lapses. Good architectures employ rate-limiting, key rotation, social or hardware recovery, and dynamic access controls to minimize these risks.
Privacy And Compliance Considerations
A delicate balance: blockchain’s immutability aids trust, but users and regulators expect “right to be forgotten” controls. Hybrid architectures store sensitive payloads off-chain and use on-chain hashes or pointers. Privacy by design becomes essential—*especially in healthcare* (Healthcare Secure Digital Identity), where consent, audit trails, and selective credential disclosure are non-negotiable.
Standards And Protocols
W3C Standards Overview
W3C DID Core and the VC Data Model anchor interoperability in the decentralized identity world. They specify data formats and trust models for issuers, wallets, and verifiers, and have robust backing across open source, enterprise, and regulatory communities.
Interoperability Layers
Interoperability is not optional—resolvers, registries, and bridges (like CAIP) ensure your DID and credentials work across chains, networks, and geographies. Adoption of Ethereum Decentralized Identity and multi-chain layers are accelerating.
Verification Flows
Flows like OIDC4VP and DIDComm codify how credentials are issued, presented, and verified. Middleware manages consent, compliance checks, and revocation—critical for scalable adoption in regulated industries.
Middleware And SDKs
Leading SDKs enable fast integration of DIDs and VCs into apps. Middleware simplifies resolving, issuing, and verifying credentials—empowering teams to focus on product, not protocol headaches (DevTo EveryCred Guide).
Protocol Stack Comparison
| Layer | Common Protocols | Strengths | Drawbacks |
|---|---|---|---|
| Identifier | DID Core, did:ethr/web | Decentralized, flexible | Custom adapters needed |
| Credential | Verifiable Credentials | Cryptographic proofs | Ecosystem maturity varies |
| Presentation | OIDC4VP, DIDComm | Consent-focused, user UX | Adoption/cross-wallet variance |
| Interoperability | CAIP, custom bridges | Cross-chain support | Added complexity/trust bounds |
Platform And Vendor Survey
Enterprise Solutions
Leaders like Microsoft Decentralized Identity, IBM, and established security vendors offer compliant, scalable, often Azure-integrated decentralized identity suites. They excel at enterprise onboarding, governance, and regulatory readiness.
Startup And Open Source Options
Dock Web3 Identity, Ceramic, EveryCred, and various community SDK projects provide nimble, developer-friendly tooling for experimental, privacy-first, or fast-moving projects (EveryCred Beginners Guide).
Domain-Based Identity Providers
Platforms like ENS, Unstoppable Domains, and hashtag-centric ecosystems (see NFT Domains Explained) let you anchor identity to a memorable, transferable web3 domain. Their integration with wallets, dApps, and affiliate marketing tools is growing rapidly.
Selection Criteria
Assess vendors on interoperability, ecosystem maturity, key-management UX, revocation tooling, and alignment with your compliance needs (Decentralized Identity Platforms Comparison).
Commercial Considerations
Commercial models range from open/public infrastructure to SaaS and pay-as-you-go. For those marketing or building a web3 affiliate marketing platform, these distinctions shape partnership, commission, and attribution flows.
Real-World Use Cases
Healthcare Identity Use Cases
Web3 identity empowers healthcare by letting patients control consent, enabling instant, verifiable credential presentation across EHRs, and improving auditability (Healthcare Secure Digital Identity).
Financial Services
Reusable KYC for DeFi and traditional finance companies vastly speeds onboarding and reduces data exposure (Ethereum Decentralized Identity), with privacy-preserving credential checks that respect user control.
Supply Chain And Provenance
Blockchain-backed credentials in supply chain mean suppliers can credibly prove product origin, compliance, and anti-fraud—streamlining recalls and audit trails (IBM Verifiable Supply Chain).
Consumer Identity And Commerce
Domain-based identity means consumers can benefit from loginless experiences, token-gated loyalty, and portable brand relationships. Owning your hashtag or NFT domain establishes a user-first commerce path (Endless Domains Ownership).
Measuring Impact
Key KPIs: fraud reduction, compliance speed, reduced onboarding friction, increased credential re-use, and growth in cross-app identity adoption.
Developer Implementation Guide
Reference Architectures
Reference setups include wallet-integrated flows, issuer-verifier separations, and modular, microservice-based credential management.
SDKs And Libraries
Whether you choose JavaScript/TypeScript SDKs, mobile wallet SDKs, or verifier backends, the ecosystem is robust and offers ready-to-integrate, privacy-preserving codebases (Dock Web3 Identity).
Testing And Staging Strategies
Utilize testnets, simulate revocation and loss conditions, and stress test with privacy edge cases.
Migration Approaches
Incremental rollout is key: coexist legacy OAuth/SAML alongside new DIDs or VCs first. Stage mature user journeys and credential recovery before cutting over.
Developer Resources And Next Steps
Experiment with Web3 Domain Platform, issue test credentials, and join standards groups.
Governance Recovery And Control
Custody Models Reviewed
- Self-custody: Full user control, highest responsibility for security
- Managed custody: Vendors hold keys, provide recovery, trade-offs for control/security
- Hybrid: Multisig, guardian models blending self-management and backup recovery
Recovery And Key Loss Solutions
Social recovery, hardware wallets, and custodial fallback offer robust solutions for regaining identity after loss (Forbes Decentralized ID 2024).
Governance For DID Networks
Method-level governance—who can update, revoke, or expire DIDs and credentials—determines stability and long-term trust.
Legal And UX Considerations
Making self-custody usable, error-minimized, and compliant with global data practices remains the greatest design challenge.
Practical User Control Limits
In real life, compliance mandates or user error may temporarily reduce perfect user control. Good ecosystems make these constraints transparent and reversible where possible.
Future Trends And Outlook
Standards convergence (W3C, Ethereum, industry consortia), ZKP adoption, and multi-chain compatibility will define the next five years. As education improves and regulatory frameworks mature, expect much more overlap between enterprise, consumer, and government digital identity.
Scenario: By 2030, cross-chain Web3 identity may allow you to use one credential wallet for voting, hiring, banking, health, and commerce—without ever “logging in” the traditional way.
Common Questions Answered
What Is Web3 Digital Identity Management?
It is the use of decentralized technologies to empower users, not platforms, as the sole controller of identity—combining DIDs, VCs, and web3 domains for seamless, secure digital life (Dock Web3 Identity).
How Does Blockchain Improve Security?
By anchoring credentials and metadata on-chain—end-to-end audit trails, tamper-proofing, and censorship resistance become possible (IBM Verifiable Supply Chain).
Which Companies Offer Solutions?
Microsoft, IBM, Dock, EveryCred, ENS, and emerging providers listed in Decentralized Identity Platforms Comparison.
Can Users Fully Control Identity?
With self-sovereign models, you control keys and credentials. However, recovery, regulatory, and usability constraints may occasionally limit this—good systems make these boundaries clear.
What Is The Future Of Identity Management?
The next wave favors seamless, cross-chain, privacy-preserving solutions driven by open standards and regulatory alignment—see Forbes Decentralized ID 2024.
Next Steps For Adoption
Actionable Next Steps
To make the most of web3 digital identity management:
- Developers: Try leading SDKs, issue a test verifiable credential, and integrate a Web3 Domain Platform domain in a demo app.
- Product teams: Pilot consent, loyalty, or authentication journeys using testnets and real world scenarios (e.g., affiliate marketing campaigns and decentralized login).
- Executives: De-risk with staged rollouts, define clear governance and compliance metrics, and review your vendor and standards strategies.
A well-executed web3 identity design improves privacy, surfaces new *user-centric business models*, and unlocks a future of trustworthy, effortless verification everywhere.
For a hands-on start: Start Experimenting With Web3 Identity.
Resources
- NFT Domains Explained
- Web3 Domain Services
- Web3 Domain Platform
- Dock Web3 Identity
- Zero-Knowledge Proofs Feature
- W3C DID Core
- Ethereum Decentralized Identity
- ArXiv Decentralized Identity Paper
- Healthcare Secure Digital Identity
- Decentralized Identity Platforms Comparison
- IBM Verifiable Supply Chain
- EveryCred Beginners Guide
- Microsoft Decentralized Identity
- Grandview Research Decentralized Identity Market
- Endless Domains Ownership
- Forbes Decentralized ID 2024
- Testsite Domains Identity Verification
- Testsite Decentralized Credentials Use Cases
- Testsite Blockchain Domains DeFi Identity
- Testsite Blockchain Domain Ownership
- Testsite Domain Lifecycle Management
- EndlessDomains Blog
- DevTo EveryCred Guide

Leave a Reply