Table of Contents
- Why Decentralized Identity Matters
- Core Concepts And Standards
- Protocols And Architectures
- Implementation And Integration
- Privacy And Recovery Techniques
- Adoption Roadmap Summary
Why Decentralized Identity Matters
Nobody wants another data breach headline. Centralized identity is a relic, a museum piece you prop up even though everyone’s tired of lockouts, hacks, and endless forms. Decentralized identity solutions in web3 ecosystem rip the façade off the old order. Here, blockchain-backed identities, built on Decentralized Identifiers (DIDs) and Verifiable Credentials (VCs), upend the idea that your information belongs anywhere except your own wallet. Control shifts—finally—from Lenovo, Google, and Facebook, straight into your hands. You think you gave up privacy for convenience. Wrong. You gave up power.
Definition And Scope
Decentralized identity solutions in web3 ecosystem aren’t a clunky replacement for old logins. DIDs, VCs, and self-sovereign identity (SSI) are the cold, hard reset. DIDs are globally unique, cryptographically anchored references to YOU—no middleman required. Verifiable Credentials (VCs) are tamper-evident proofs of anything: skills, KYC, or domain ownership, cryptographically signed, forever portable. SSI means individuals—not providers—operate the levers of identity, from creation to selective disclosure. Only web3 domains for identity make digital identity future-proof.
User Control And Privacy
Privacy happens when you rip out the root of surveillance. In this world, you—yes you—hold the cryptographic keys. Centralized databases sell, leak, and lose your data. With decentralized identity, selective disclosure using VCs means you never show more than you wish. No forced logins. No marketing profiling by silent partners. Web3 digital identity guide shows how granular privacy finally gets teeth: your keys, your data, your rules.
Why It Matters Today
Creatives don’t just want followers, they want control. Creators use self-sovereign identity for digital creators to authenticate work, monetize personas, and shake off platforms that profiteer their presence. Startups rip onboarding friction out of the funnel with decentralized identity for startup user onboarding—KYC that isn’t a growth-killer. Service providers swap brittle logins for verifiable trust, moving cross-chain and cross-platform. Centralized identity is obsolete the second your competitors unlock seamless onboarding, zero-knowledge KYC, and digital wallets as login. Wait, and you’ll chase their users forever.
Centralized vs Decentralized Identity
| Aspect | Centralized Identity | Decentralized Identity |
|---|---|---|
| Control | Provider controls credentials | User-controlled keys; no central server |
| Privacy | Data shared broadly | Minimal disclosure via VCs |
| Recovery | Provider-managed | User-Guided (guardians/social recovery) |
Core Concepts And Standards
Burn old definitions. Decentralized identity foundation delivers digital identity without rent-seeking gatekeepers. You don’t sign up; you self-assign. DID, VC, and wallet: these are your passport, proof of skill, and bank vault, all in one.
What Are Decentralized Identities?
A DID shatters the passport model. It is a globally unique, cryptographically secure identifier owned by its subject, not conferred by governments or corporates. Every decentralized app, wallet, and service in Web3 integrates these primitives—not as an option, but baseline. Account-based identities are yesteryear. Web3 dares anyone to forge, counterfeit, or hijack a decentralized identity foundation credential: fail. The explosive use cases: onboarding, KYC, age-check, or domain authority—without paper-trails or data leaks.
How Decentralized Identity Works
Here’s the killer move: cryptographic proof, not trust in admins. Every DID resolves to a document, signed by private keys in your control. Registries operate on-chain or off, no single authority gets the monopoly. You issue and manage VCs—your degree, job credential, art portfolio—signed and verified without leaking your life story. Registries span blockchains or web domains; resolvers read, validate, and enforce. Every Wallet—Metamask, Azure, proprietary—plugs into this verifiable mesh. Verifiable Credentials Spec lays the ground rules. DID Methods dictate if your identity lives on Ethereum, your own domain, or mere keypairs.
Key Standards And Roles
This is the era of standards trumping silos. W3C’s DID Core Specification is non-negotiable. Verifiable Credentials standard (Verifiable Credentials Spec) makes interoperability the expectation. Identity Foundation drives global consensus; decentralized identity foundation aligns the incentives. Wallets act as relays, issuers mint VCs, holders store and present, verifiers challenge and accept—each role cryptographically defined. Try breaking this chain.
DID Methods Comparison
| DID Method | Decentralization | Discoverability | Best Use |
|---|---|---|---|
| did:ethr | Blockchain-tethered | High | EVM ecosystems |
| did:web | DNS-based | Medium | Web services, domains |
| did:key | Key-first | Low | Device identities |
Protocols And Architectures
Forget login forms, Trusted Third Parties, and data honey-pots. Web3 digital identity guide swaps them for cryptographic assurances and fatally reduces reliance on arbitrary admin approval. You want trust? The only source is the math.
Resolvers And Registries
DIDs resolvers are the switchboard operators of Web3 identity. Input a DID, and receive the keys and endpoints tied to it, verifiable on-chain or via DNS proofs. Registries store mapped documents, anchored in blockchains for the chains, and web servers for non-chain DIDs. Tradeoffs are blunt: on-chain systems (did:ethr) win at transparency and censorship-resistance, web-based methods (did:web) dominate for legacy compatibility and speed.
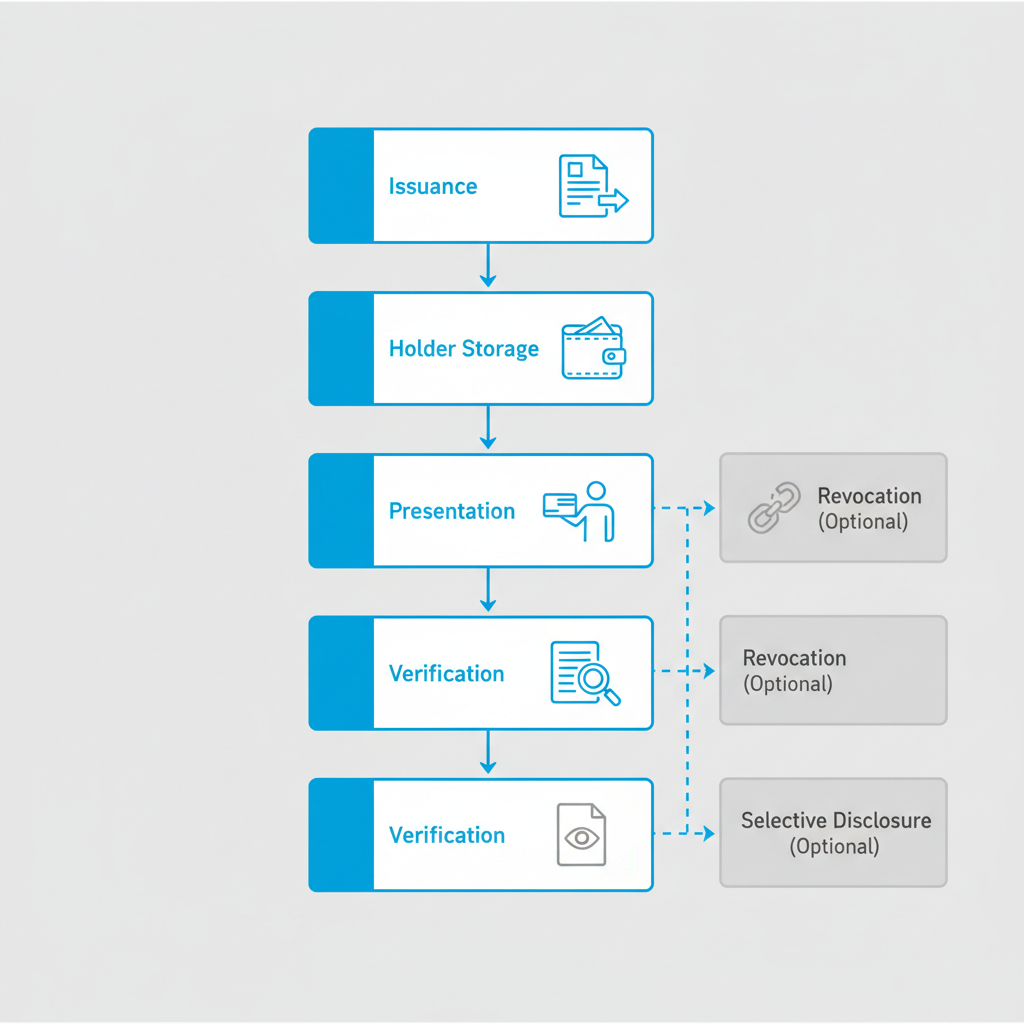
Verifiable Credential Lifecycle
Verifiable Credentials are never static. Their life looks like this:
- Issuance: Authority (school, KYC provider, platform) signs and grants your credential.
- Holder Storage: Drop it in your digital wallet—your private vault.
- Presentation: You selectively reveal only what’s relevant, never oversharing.
- Verification: Counterparty inspects cryptographic proof—zero trust in mere words.
- Revocation (Optional): Issuer cancels a VC; you see it instantly.
- Selective Disclosure (Optional): Prove a fact, not your entire identity, via ZKPs.
SSI For Creators
Digital creators are no longer hostages of platform monopoly. Self-sovereign identity for digital creators hands creators both authentication and monetization levers. No middleman owns your domain, your persona, or your earning hooks. NFTs and Web3 domains fuse reputation and ownership. Monetize with credential-gated content, direct affiliate bounties, and micro-licensing using web3 domains for identity. Reputation isn’t legacy likes and follower counts—it’s proofs you own, impossible to fake or transfer away. Platforms supporting SSI: UNSTOPPABLE DOMAINS, ENS, and emerging DAOs for art, music, and knowledge products.
VC Format Comparison
| Format | Privacy | Compactness | ZKP Friendly |
|---|---|---|---|
| JSON-LD VC | High semantic richness | Larger payloads | Supports proofs |
| JWT VC | Compact and familiar | Compact payloads | Less ZKP support |
| BBS+ VC | Designed for disclosure | Moderate size | Strong ZKP support |
Implementation And Integration
Still think only FAANG can build digital identity? Wrong. The blueprints are open, the tooling mature, and the ROI for brave teams—massive. Web3 digital identity guide and did vc integration checklist slice through the confusion.
Developer Checklist And Tools
Teams must stamp out excuses. Here’s your critical path:
- Choose a DID Method: On-chain (did:ethr), domain-based (did:web), or key-derived (did:key)?
- Select Wallet/Agent Libraries: Use Hyperledger Aries for agents, Metamask/CLI for wallets.
- Integrate VC Issuance: Stand up an issuer—any KYC provider, employer, or authority.
- Adopt Verified Presentation Flows: Wallet-based or server-based challenge-response flows.
- Test and Harden: Try revocation, expiration, and presentation under adversarial scenarios.
- Roll Out With Pilots: Onboard users, creators, or affiliates with real-world use.
did vc integration checklist streamlines your entire build.
Onboarding And User Flows
Neobanks grow 2x faster when onboarding is frictionless. Decentralized identity for startup user onboarding hijacks the KYC process, compressing multi-day checks to seconds. Instead of asking for 3 forms of ID and feeding legacy credit bureaus, apps request a verifiable credential, issued by a trusted party, and validate instantly. Less friction, less fraud, less user dropoff. The only losers: rent-seeking data brokers and traditional onboarding vendors.
Recovery And Governance Patterns
Ignored recovery is how platforms die. Social recovery uses trusted peers (guardians); multisig wallets split power among several keys; custodial setups add a fallback. recovery and governance guide lays out practical patterns: combine threshold cryptography, on-chain contracts, and external identity claims for bulletproof protection. Governance templates sidestep single admin risk—the community, not one boss, controls recovery.
Auth And Verification Options
| Approach | User UX | Security | Developer Effort |
|---|---|---|---|
| Wallet-Based Presentation | Seamless UX | High (crypto proof) | Medium (wallet req) |
| Server-Side Verification | Transparent | Medium (key custody) | High (backend req) |
| OAuth Bridge | Familiar flows | Low (less decentralization) | Low |
Privacy And Recovery Techniques
Centralization poisons privacy. Web3 domains for identity and VCs, paired with ZKPs, deliver privacy without “trust us” promises.
ZKPs And Selective Disclosure
Zero-Knowledge Proofs (ZKPs) and BBS+ credentials let you prove what’s needed—nothing more. Want age verification without leaking your birthday? Or that you’re KYC-verified but not by whom? Privacy With ZKPs breaks open possibilities. No more mass data leaks to satisfy petty compliance.
Custody And Key Management
Messy key management doesn’t justify sticking with Gmail logins. Custody puts private keys in your hands (non-custodial), lets you delegate to a service (custodial), or blend both (hybrid). Hardware wallets, secret shares, and threshold schemes are advancing fast. Ditching passwords for cryptographic keys isn’t just better—it’s a shutdown for phishing.
Governance And Recovery
Recovery isn’t a helpdesk ticket. Social recovery lets trusted friends restore lost access. Multisig contracts require quorum for critical moves. Custodial fallback offers mainstream familiarity at privacy’s cost. recovery and governance guide offers real-world-tested playbooks for founders and teams.
Recovery Methods Comparison
| Method | Security | User Ease | Complexity |
|---|---|---|---|
| Social Recovery | Medium | High | Requires trusted peers |
| Multisig Wallets | High | Medium | Smart contract setup |
| Custodial | Low | Very Easy | Provider dependence |
Adoption Roadmap Summary
Teams refusing to pilot decentralized identity dig their own grave. The migration is happening. Those shipping web3 domains for identity and verifiable credential flows gobble the next decade of Web3.
Next Steps For Teams
Abandon perfectionism, start small:
- Select one DID method aligned with your users.
- Run a pilot for onboarding or creator credentialing.
- Integrate basic VC issuance, plug into wallets.
- Plan governance: multisig, threshold recovery, and frictionless escalation.
- Monitor, harden, iterate. Don’t get left behind.
Key Resources
The playbooks and standards:
- web3 digital identity guide
- did vc integration checklist
- recovery and governance guide
- DID Core Specification
- Verifiable Credentials Spec
- Identity Foundation
Resources
- DID Core
- Verifiable Credentials
- Identity Foundation
- Azure Verifiable Credentials
- Hyperledger Aries
- OpenID VC Working Group
- ZKProof
- Consensys Decentralized Identity
- Dock Web3 Identity
- Hashtag.it Decentralized Identity Foundation
- Web3 Digital Identity Guide
- Web3 Domains For Identity
- Recovery And Governance Guide
- Developer DID/VC Checklist

Leave a Reply